Debug The App With Chrome
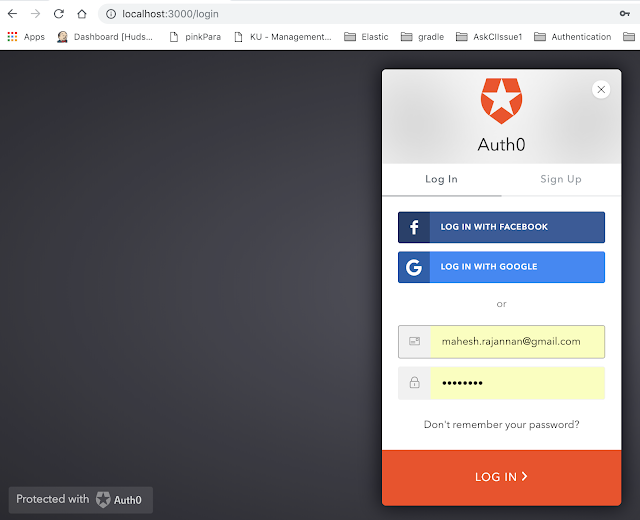
DEBUG THE APP. 1. Enable Chrome Developer Tools. 2. Click Login and see the login page. a. Check the developer tool configuration. 3. The federated login page. Note : The federated login page is injected by lock.min.js 4. Observe the Requests. Note :Observe the client id, it is the same as the Auth0 settings page. 5. On click Auth0Login. The call goes to Auth0 server and client id is passed. 6. Examine Authorize. Note : a. client id. b. response type param is code. c. redirect uri is http://localhost:3000/callback, as we initialized in our code Auth0 page. d. scope is email id, name and picture(Which is not available for me). e. realm username-password-authentication, the grant type basically. f. Explore request headers and response headers. g. Headers are chosen, instead of other params, for security reasons. h. Note the set-cookie (http secure) under response header. i. The authorization code under response header(7pmf*****cbl) .